M.S. Candidate: Sinan Düztaş
Program: Cybersecurity
Date: 16.01.2026 / 11:00
Place: Cisco Lab
Abstract: Cyber threat actors (CTAs) rely on botnets to carry out a wide range of malicious operations. These botnets are controlled by command-and-control (C2) servers. If these servers are exposed, CTAs can be detected and their activities can be disrupted. In order to disguise their C2 servers, CTAs employ domain generation algorithms (DGAs). These algorithms produce large number of random domain names. CTAs use DGAs to bypass traditional detection mechanisms like blacklisting or static signature-based solutions. Since blacklisting all DGA-generated domains is not possible, the automatic detection of DGAs remains a critical necessity.
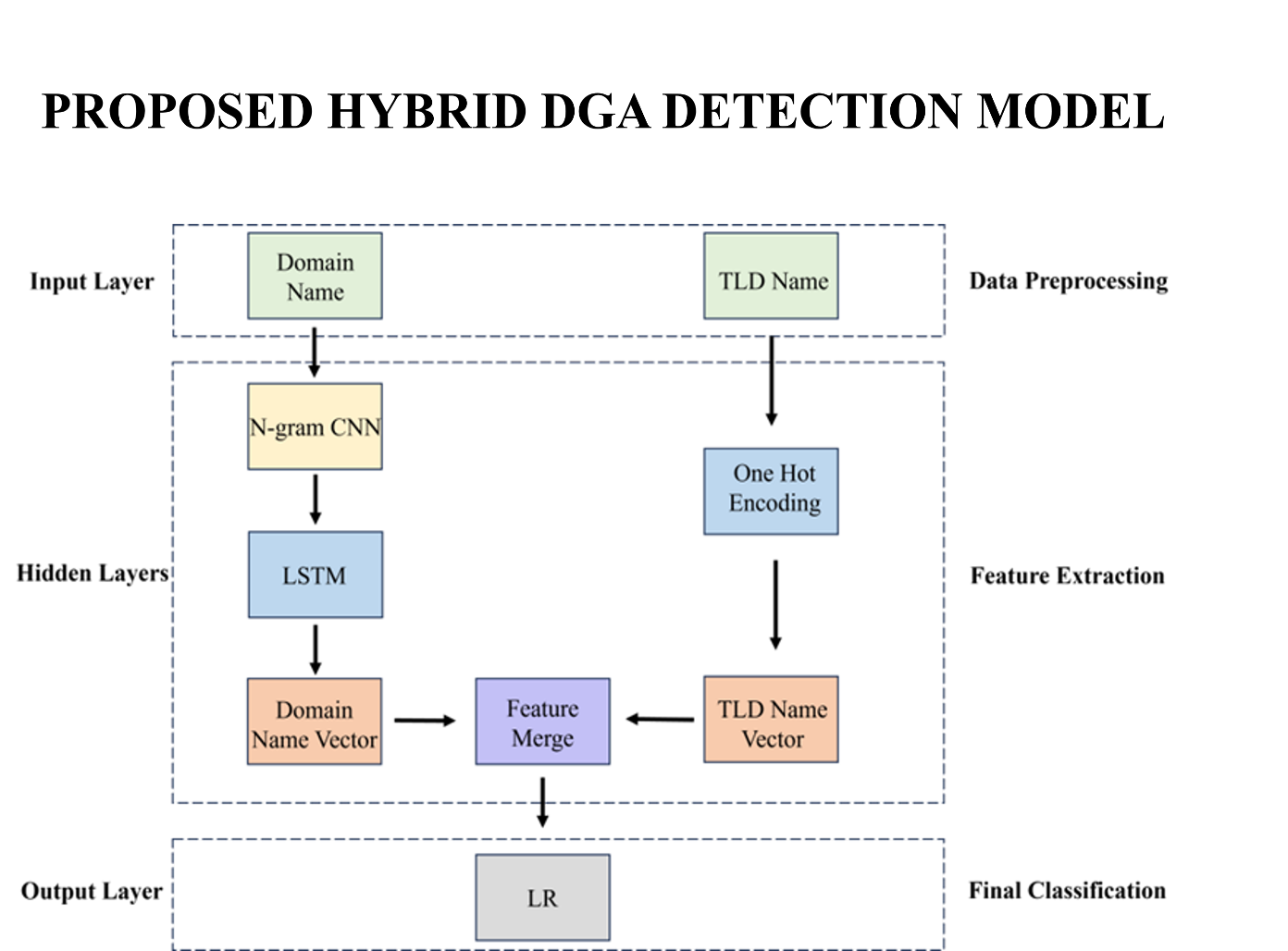
The problem of distinguishing legitimate domains from DGA generated domains is an ongoing challenge. Despite years of research, modern malware continues to evolve, and this makes detection increasingly difficult. Traditional machine learning models for DGA detection heavily rely on verbal analysis of domain names through manual feature engineering. However, these models are time-consuming to construct and often produce high false positive rates. This thesis addresses these limitations by employing a hybrid framework that integrates CNN based n-gram learning and LSTM for automatic feature extraction and Logistic Regression (LR) for final classification. The model input is further enriched by Top-Level Domain (TLD) information for improved accuracy. The model is trained with a publicly available dataset compiled from ICANN, Alexa and DGArchive. Its performance is compared against other deep learning models like CNN, LSTM, GRU and Transformers. This research aims to contribute to the cybersecurity domain by offering a comprehensive solution for detecting DGAs through a novel hybrid framework that enhances overall detection performance.